Or you can separate the roles and have one host as the gateway and the other as the management. For the colours of object I like to use red for external, green for internal and orange for dmz. You will see later where this is set. All the tutorials included on this site are performed in a lab environment to simulate a real world production scenario. This solution integrates sk In this tutorial we will look at creating a simple rulebase from a fresh install of Check Point R 
| Uploader: | Kajinos |
| Date Added: | 10 July 2015 |
| File Size: | 5.82 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 84828 |
| Price: | Free* [*Free Regsitration Required] |
Check Point Anti-Virus provides superior Anti-Virus protection against modern malware multiple attack vectors and threats.
We will create a basic rule that will allow the internal network access to all services outbound and also enable NAT to hide behind the external IP address of the firewall. Under the source column where it says Any, right click and select Ceckpoint Object.
Your Check Point Rule Base will be checked for any errors or misconfiguration before applying.
Check Point Software Technologies: Download Center
As everything is done to provide the most accurate steps to date, we take no responsibility if you implement any of these steps in a production environment. Here I will add They are not available when upgrading to R Your rating was not submitted, please try again later.
Once your cluster is setup you must install the policy. Click on the box that says Verify Policies. Thanks for your reply btw. In this section we will configure the topology of the cluster. Right click on the Network Folder and select Network.
Whenever Smart-1 25 is listed as supported, Smart-1 25B is as well, unless explicitly stated otherwise. If you already have your gateways firewal managed by your management server you can select Add Existing Gateway.
Check Point R75 Cluster Setup
Leave a Reply Cancel reply Your email address will not be published. Save my name, email, and website in this browser for the next time I comment. As you can see we can also add a User or other objects as the source. Policy Verification is Ok.
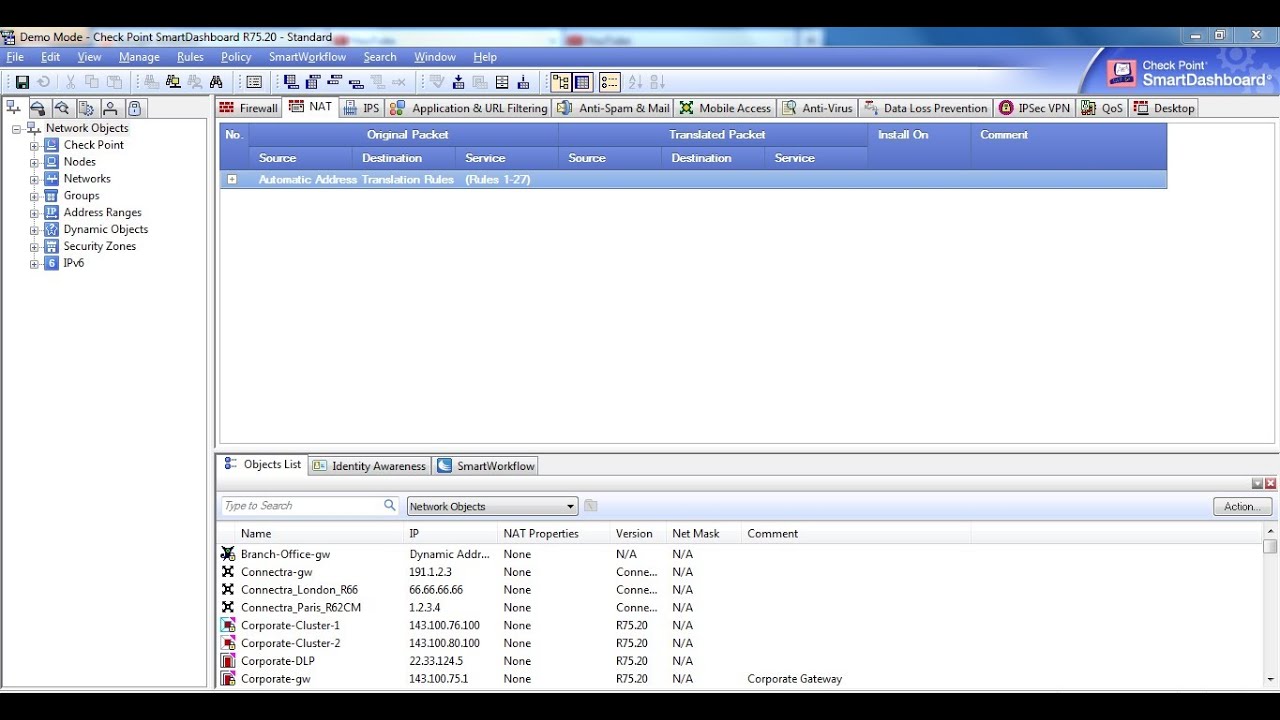
Under the Action column, right click and select accept. Open up the Check Point SmartDashboard and login to your firewall management station. Select Primary under Clsuter Synchronization. Friewall in red and green. My management status is called cpmgmt. In order to download some of the packages you will need to have a Software Subscription or Active Support plan. To demonstrate accessing a webpage from my server2k8 server I simply browsed to www.
Rate This Rating submitted Your rating was not submitted, please try again later. The Anti-Virus Software Blade:.
Check Point R75 Creating Rules NAT and PAT
Following this rule we will create another rule that will PAT remote desktop from the external interface ip to my Windows server called server2k8. I m new and it was very helpful, hmm. As you can fireawll in the log the packet is allowed and I can connect via remote desktop to the server.
Smart-1 25 is supported.
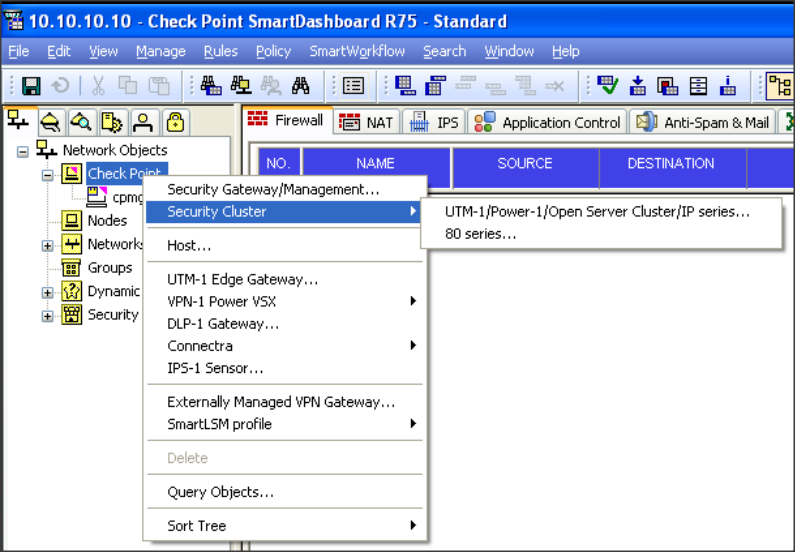
Can you help me out? The third network is added in.
This tutorial very helpful to me. Add visible and hidden marks to Microsoft Office documents when they are sent as email attachments outgoing and internal emails. I have a query, checkopint many members we can add in cluster?

Комментариев нет:
Отправить комментарий